SYN Flood Attack Disrupts Hospital Network Infrastructure
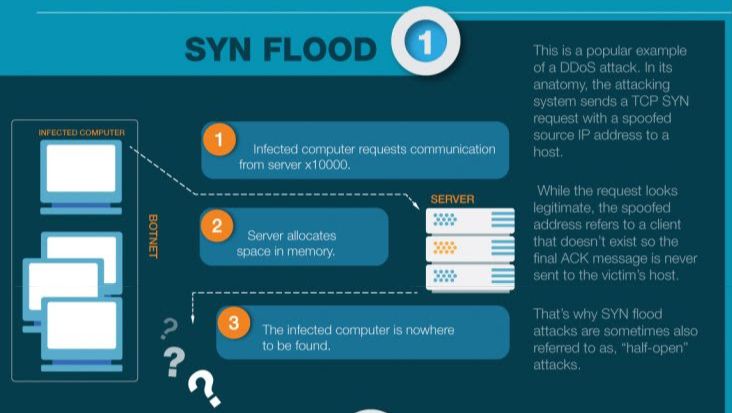
A major hospital in **Mumbai, India**, faced a severe SYN flood attack on its internal network infrastructure earlier this week. The distributed denial-of-service (DDoS) attack flooded the hospital’s servers with thousands of fake connection requests, crippling communication systems and halting real-time access to patient data. The hospital’s emergency response team had to revert to offline procedures for over eight hours, impacting appointment scheduling and digital patient monitoring systems.
Cybersecurity analysts suspect that the attack originated from a botnet operated outside India, possibly targeting the hospital as part of a broader campaign against critical infrastructure. While no data exfiltration has been confirmed, IT staff noted unauthorized traffic surges and potential probes into backend services during the attack window. The hospital has since involved the Indian Computer Emergency Response Team (CERT-In) to assist in forensic analysis and network fortification.
This incident has raised alarm bells across India’s healthcare sector, prompting other hospitals to conduct immediate audits of their network security protocols. Experts are urging institutions to deploy robust DDoS mitigation tools, isolate critical systems from public interfaces, and establish faster incident response mechanisms. The attack serves as a reminder that even life-saving services are not immune to modern cyber threats.
← Back to News